I’ve recently ran into a few times where we had to move a certificate from Microsoft Exchange to a HAProxy load balancer. I was provided an exported key pair that had an encrypted private key (Password Protected).
We will seperate a .pfx ssl certificate to an unencrypted .key file and a .cer file
The end state is to get the private key decrypted, the public cert and the certificate chain in the .pem file to make it work with openssl/HAProxy.
Requirements:
Openssl installed
.pfx file (you need to know the password)
intermediate public cert (you can obatin this from your provider like Thawte)
root public cert (you can obatin this from your provider like Thawte)
Step 1
Extract the private key from the .pfx file (you need to know the password:
openssl pkcs12 -in [certificate.pfx] -nocerts -out [certificate-key-encrypted.key]
Step 2
Now lets decrypt the key:
openssl rsa -in [certificate-key-encrypted.key] -out [certificate-key-decrypted.key]
openssl rsa -in [certificate-key-encrypted.key] -out [certificate-key-decrypted.key]
Step 3
Now lets extract the public certificate:
openssl pkcs12 -in [certificate.pfx] -clcerts -nokeys -out [certificate.crt]
Step 4
You also need all the public certs in the chain up to the root. I’m talking about these:
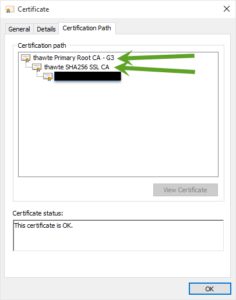
Step 5
now create a new text file (don’t use notepad) and put your public, private, intermediate public and root public together. It’s simple and should look like this:
-----BEGIN CERTIFICATE----- ### Replace with your public certificate ### ### From step 3 above ### -----END CERTIFICATE----- -----BEGIN CERTIFICATE----- ### replace with your intermediate public cert ### -----END CERTIFICATE----- -----BEGIN CERTIFICATE----- ### replace with your root public cert ### -----END CERTIFICATE----- -----BEGIN RSA PRIVATE KEY----- ### replace me with your .key file ### ### from step 2 above ### -----END RSA PRIVATE KEY-----
Save the file as a .pem file.
If you want to view the cert on windows, simply rename the .pem to .cer
…This is how Ed does it 🙂
When I run step 1, I don’t get a usable encrypted key. I get the text of what the key represents only. Then when I try to use that file for step 2, I get the error:
unable to load Private Key
I’m assuming you threw away the actual encrypted key data with the “-nocerts” option?
You exported the private key of the certificate in step 1 but it should have been encrypted. Did you ever find out what went wrong?